top of page


Industry Insight: Cloud Security Is Shifting Left; Here’s What That Means for Enterprise
n a shift left model, security is no longer the sole domain of a separate security team. Instead, developers are empowered and expected to take ownership of security. This involves using automated tools to scan code for vulnerabilities as it's written and implementing security best practices throughout the development process. By doing so, security keeps pace with development, allowing teams to build and deploy software that is both innovative and secure, without sacrificing
3 min read


Know why Secure Landing Zones are Non-Negotiable in Cloud Adoption
Increasing cloud footprint and adoption of cloud services becoming a strategic imperative for businesses looking to stay competitive and...
5 min read


Transforming Enterprises with Secured Cloud Automation: Atsky’s Success Stories
As enterprises increasingly shift to the cloud, the need for secure, automated, and scalable solutions has never been more critical. At...
4 min read


Navigating the NIS2 Directive: A Guide
The digital landscape is evolving rapidly, and with it, the threats that organisations face in terms of cybersecurity are becoming more...
4 min read


Atsky Initiative: Navigating the Complexities of Modern Architectures
Modern technological frameworks like containers and Kubernetes bring forth immense advantages but also pose distinctive challenges. In...
3 min read


A Simplified Guide to Kubernetes Management and Tools
Overview of Kubernetes Management Managing a Kubernetes cluster isn't a walk in the park—it requires specialized tools that help you get...
5 min read


Navigating the Cybersecurity Landscape: CASB vs SASE
In our increasingly digital era, businesses are leaning more on cloud services and remote access. This shift has made cybersecurity not...
3 min read


Exploring the New Support for Security Groups in Network Load Balancers
The realm of cloud computing witnesses constant evolution to cater to the dynamic needs of businesses. In a significant stride towards...
2 min read


Secure Management of Database Credentials in an Amazon ECS Cluster
In today's era of cyber threats and stringent data privacy regulations, secure management of sensitive data such as database credentials...
5 min read


Cloud Security Unlocked: Essential Best Practices for IAM in Cloud-Native Infrastructure
As businesses transition from on-premises infrastructure to cloud-based solutions, managing digital identities and access to resources...
10 min read

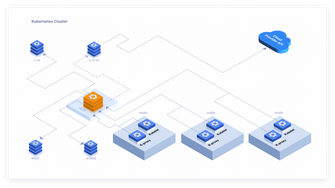
Getting Started with the Kubernetes API
Kubernetes has emerged as the leading container orchestration platform, which makes it easier to manage containerised applications at...
4 min read


Ensuring secure residence of critical data workloads with network segmentation and Control Tower
In today's digital landscape, the secure residence of critical data workloads is of utmost importance for organizations. To achieve this,...
3 min read


Ensuring GDPR Compliance and Data Protection in the Cloud
As hybrid working becomes the norm and more data is stored in the cloud, organizations face complex security challenges. To ensure that...
4 min read


Understanding NAT Gateway for AWS: A Comprehensive Guide
What is a NAT Gateway and how does it work? NAT Gateway is an essential service that enables instances in a private subnet to connect to...
5 min read


Kubescape or Falco? Choosing the Right Kubernetes Security Tool for Your Environment
What is Kubescape? Kubescape is an open-source tool developed to scan Kubernetes clusters for security risks, including...
4 min read
bottom of page

